Table of Contents
What is mean by encryption and what are the different types of encryption?
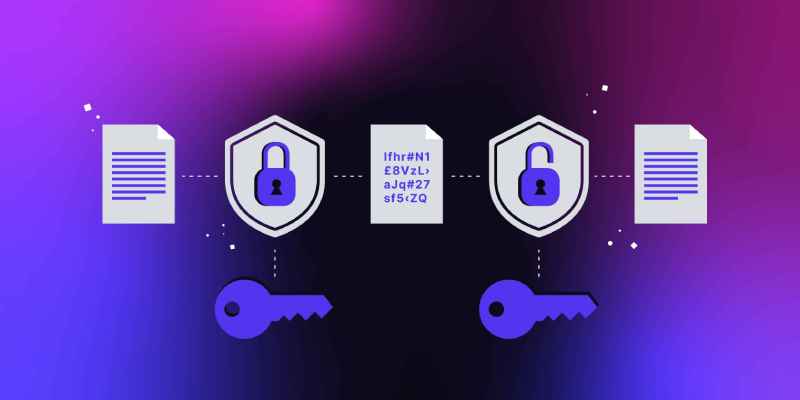
Asymmetric or Symmetric Encryption – The answer depends on what you use it for. But first, it helps to simply understand what encryption actually does. Encryption encrypts your data so that only people with the key can access it
Encryption involves encrypting data so that only authorized users can access it. There are different types of encryption, but two of the most common are asymmetric and symmetric.
What are the differences between asymmetric & symmetric encryption?
Asymmetric encryption uses two unlike keys to encrypt and decrypt data. One key is used for encryption, the other for decryption. This means that securely sending encrypted data to someone requires them to have both required keys. Since only one key is shared, it is easier to secure this type of encryption. However, if one of the keys is compromised, the entire system will fail.
Symmetric encryption uses a single key to decrypt & encrypt data. This means that when you send data encrypted using this type of encryption, the recipient must know the key to unlock it. Since only one key is used for encryption and decryption, symmetric encryption is faster to use, but it is more difficult to ensure security because the likelihood of a key being compromised is higher.
When should each type of encryption be used?
Most commonly, asymmetric encryption is used to authenticate and encrypt small amounts of data that can be decrypted by multiple parties because it is easier to manage than symmetric encryption.
Asymmetric cryptography ensures confidentiality, integrity, authentication and non-repudiation.
Symmetric cryptography only provides data protection, but is much faster at encrypting large amounts of data. This type of encryption is often used to encrypt things like passwords or small files that are shared with a single person.
If you have very high security needs, it is better to use asymmetric encryption, as this type of encryption is more secure. Because asymmetric keys are easier to keep secret, this type of encryption also provides non-repudiation security so that the sender cannot subsequently pretend that they did not send a message.
Asymmetric cryptography ensures confidentiality, integrity, authentication and non-repudiation, while symmetric cryptography only ensures confidentiality.
It is essential to use strong passwords to safeguard your data
You must use a unique, randomly generated password for each online account you have. Make sure it is at least 12 characters long and contains a combination of uppercase letters, lowercase letters, numbers and symbols. Avoid using dictionary words or personal information such as your name, date of birth, or your pet’s name.
Tips for Creating a Strong Password
Use three random words to form the core of your password. For example “Weepy&Sensitive&Dolphin”. You can replace any word in this sentence with a specific number if it makes grammatical sense. For example, “Weepy$&Sensitive&Dolphin” becomes the password “Weepysensitivedolphin”. To further improve security, you can replace any word in this sentence with a foreign word that you do not understand. For example, using French words would result in the password “Jolie&Attentent&Girafe”.
When should you avoid symmetric encryption?
You should not use symmetric encryption if it is not necessary. For example, secure transmission of a password over the Internet is better suited to asymmetric encryption because multiple people generally do not need to access the same data.
If possible, it is best to avoid symmetric encryption and store your password in an encrypted file accessible on demand from any device with Internet access. Re-encryption and decryption take a lot of time and energy, so it’s best to use asymmetric encryption for this purpose because you only need one key to encrypt and decrypt the data.
Conclusion
Regardless of what type of encryption you use, it is important not to forget your password. Additionally, you should always avoid storing your password in a file on any device. This could potentially be access from the Internet without using encryption.
If possible, it is recommended to use asymmetric encryption to protect passwords. And only use symmetric encryption when necessary.
ALSO READ: 7 Key Benefits of opting .NET for Web Development in 2024
ALSO READ: 6 Best AI Song Generators for Taylor Swift Fans
- Drones: Basic Uses, Information, Features & More – 2024 - April 9, 2024
- When to Use Asymmetric vs Symmetric Encryption - April 8, 2024
- 7 Key Benefits of opting .NET for Web Development in 2024 - April 6, 2024