Most current messaging service providers use end-to-end encryption on their platforms. (Among others, WhatsApp, Zoom, and Facebook)
Although “encryption” conjures up images of reliable cybersecurity, what does end-to-end encryption entail? Data that has been encrypted cannot be read without a decryption key, which is simple to obtain.
However, how does “end-to-end” fit in? What are the advantages for users?
Let’s investigate and learn more.
Table of Contents
End-to-End Encryption: What Is It?
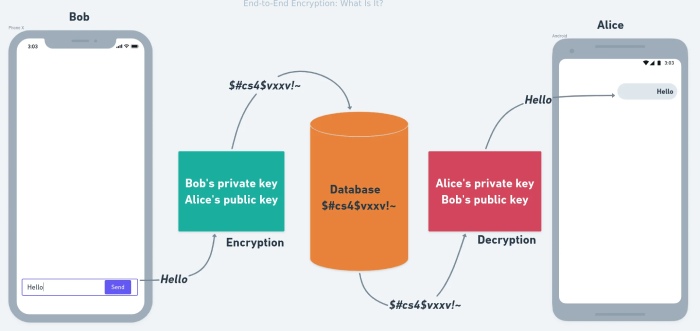
End-to-end encryption, often known as E2EE, is a safe method of communication that forbids any outsider from reading data. At the same time, it is being transferred from one end device or system to another.
Data sent through E2EE is encrypted on the transmitting device before traveling over a secure path to the recipient, where only they can decrypt it. App service providers, internet service providers (ISP), or hackers traveling with the communication cannot read or corrupt it.
How Does E2EE Function?
The center of E2EE is a cryptographic key that encrypts and decrypts messages and exists on the communication chain’s endpoints. Public-key encryption is used in such a strategy.
Public-key encryption, often known as “asymmetric” encryption, gives you a private key that you can use to decrypt messages and a public key that you may share with others to encrypt their messages.
Senders can use your public key to encrypt a message and send it to you after giving them access. After that, you can decode the data using the associated private key. (sometimes referred to as “a decryption key.”
We’ve all had experience with the fact that messages are typically sent between parties in online discussions by an intermediary. It might be an ISP, a telecommunications provider, a social media website, or something else entirely. No matter the nature of the intermediary’s services, E2EE ensures they shouldn’t be able to listen in on your private talks.
What Threats Does End-to-End Encryption Guard Against?
E2EE offers a defense against message tampering and prying eyes, the two main risks to communication.
End-to-end encryption prevents anyone besides the intended recipient from accessing the transferred data. It’s as if you shipped a titanium box chained and locked with various high-tech padlocks, and the only person who possesses the keys to any of them is the recipient.
Although it would be difficult to conceive such a conversation in the real world, it is simple to do so online. To preserve the secrecy of communications, encryption experts are also continually creating new encryption techniques and strengthening existing ones.
E2EE also ensures the integrity of private messages in addition to privacy. Nobody can decipher and alter your message, even if it is intercepted in transit. Modern encryption makes it impossible to modify a statement and have it appear valid upon arrival. Suppose the message is changed while it is being transmitted. In that case, the recipient will see a jumbled collection of symbols when it is decrypted, which is a surefire indication that the communication was tampered with.
Now, both communications integrity and privacy are taken care of. E2EE does not, however, automatically solve every data transmission issue.
What Is Not Protected Against by End-to-End Encryption?
The totality of your communication is encrypted by E2EE, making it a vital cybersecurity asset that only the recipients can decrypt. E2EE, however, does not conceal the fact that you have spoken with a specific person.
Although the computers cannot read the messages you have sent and received, it is clear that you have spoken at a specific time and day.
Additionally, anyone with access to your communication device can view, listen to, and join your conversation. Therefore, even if you merely use a PIN code, reasonable E2EE offers enough device and app protection in case your smartphone is lost or stolen.
It is best to utilize antivirus software to ensure your communication remains confidential.
Malware can access the communication even if your gadget is on your person and let outside parties read your correspondence as if they were holding the device. Furthermore, even if you take all the necessary precautions to secure communications, your recipient might not, in which case end-to-end encryption is useless.
End-to-End Encryption: Why Is It Important?
End-to-end encryption is essential since it offers users a secure channel for communication. Until they are received and decrypted by the recipient, messages, emails, and attachments remain encrypted.
This is essential for both private and professional communications.
Remember that services like Yahoo, Microsoft, and Google have copies of the decryption keys belonging to users and have access to the information you send and receive. A well-designed E2EE system limits providers’ access to the decryption keys.
End-to-End Encryption’s benefits
Let’s go over the main benefits of E2EE to summarise.
protection from hacking
Hackers cannot correctly access the supplied data since only you have the private key to decrypt it.
Privacy
Only the sender and receiver can access communication details on an adequately constructed E2EE system. Your messages are entirely private, not even to the communication service provider.
Tamper-proof
E2EE prohibits the transfer of a decryption key. No hacker can intercept it in transit because the recipient already possesses one. Even if the message is altered, the recipient will be alerted to the alteration upon proper decryption.
Compliance
A company can secure its data using end-to-end encryption to render it unintelligible to outsiders.
Admin defense
Server administrators typically don’t own decryption keys. Therefore, hacker assaults against them won’t be as effective.
Also read:- An Overview of Employee Time Clocking Apps to Replace Manual Time Sheets
- Drones: Basic Uses, Information, Features & More – 2024 - April 9, 2024
- When to Use Asymmetric vs Symmetric Encryption - April 8, 2024
- 7 Key Benefits of opting .NET for Web Development in 2024 - April 6, 2024